Internet Explorer — Disabling SSL2, SSL3 [CVE-2014-3566]“SSL” — Secure Sockets Layer — is a widely-used description for what is actually a family of encryption protocols for the transmission of data across the internet. In fact, after the release of SSL 2.0 and SSL 3.0, the technology was renamed to Transport Layer Security (TLS) and the numbering restarted at TLS 1.0, then TLS 1.1 & 1.2 and lately TLS 1.3. So “SSL” is somewhat of an anachronism but most people have a notion of what it relates to. The newer encryption protocols are, naturally, better and more secure, and harder, if not impossible, to crack. But the older protocols are rapidly changing from being theoretically crackable to easily crackable, and thus have become dangerous to use. For example, SSL 2.0 has been widely regarded as insecure for many years. Modern browsers disable the use of SSL 2.0, and it would only be enabled, hypothetically, if it was necessary to connect to a webserver which only accessible over https using SSL 2.0. This should be very rare. SSL 3.0 has long been regarded as relatively weak, but not dangerously so. However, in October 2014 it became known that a serious weakness in SSL 3.0 can allow a man-in-the-middle attack which can trigger code execution. “The Internet” collectively, has decided that now is the time to finally deprecate the use of SSL 3.0, and various client-side and server-side software is being updated to remove it. Attacking the weakness in SSL 3.0 requires both a vulnerable server and vulnerable client, so it can be mitigated easily by disabling SSL 3.0 on web browsers. Chrome and Firefox are being updated to remove SSL 3.0, but for business networks with many flavours of Windows and Internet Explorer, waiting for binary updates to disable SSL 3.0 may be impractical, given the use of SSL 3.0 should be discontinued very quickly. For Windows/Internet Explorer, disabling SSL 3.0 can be achieved with Group Policy and manual configuration of the browser. Also, a command suitable for login scripts etc is: reg add "HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings" /v SecureProtocols /t REG_DWORD /d 2688 /f In this command, 2688 consists of 128 + 512 + 2048, which represents enabling TLS 1.0, TLS 1.1 and TLS 1.2 respectively. (SSL 2.0 and SSL 3.0 are represented by 8 and 32.) Thus only the post-SSL 3.0 encryption suites will be enabled. Note that only Windows 7 and above support TLS 1.1 and above, but this command will still work on Windows XP/2003/Vista/2008 because the value is a bitmap. To configure these protocols manually, go to Tools → Internet Options → Advanced: 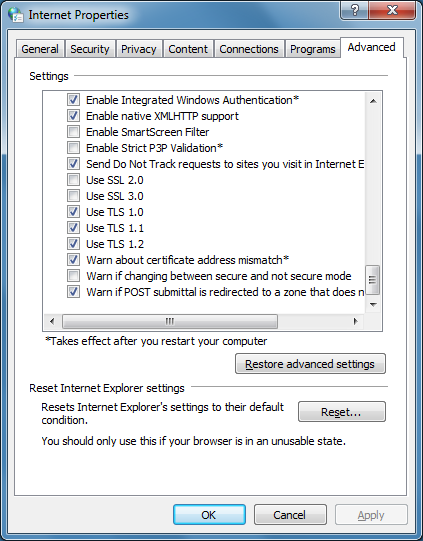 You may also wish to explicitly block SSL3 Fallback with the following command: reg add "HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings" /v EnableSSL3Fallback /t REG_DWORD /d 0 /f By default this option is off anyway. |