Phishing TripsWhat Is Phishing?Phishing is an attempt by a hacker to trick you into revealing some personal information, such as credentials for online banking or credit card details. The most common method is emails which look like legitimate communications from trusted companies, such as Ebay, Paypal, Amazon or a bank, asking you to click the link in the email to log in to their system to reset your password, to make sure your account is working, or to gain access to new features. When you click the link you are taken to a website under the hacker's control and any information you provide is fed straight back to them. Phish attacks are almost always random; if you bank with Westpac, and you receive an email purportedly from Westpac, the hacker/spammer has no specific knowledge that you bank with Westpac. It is just a shot in the dark. You are equally likely to receive one that claims to be from other banks. But in the future the incidence of phish attacks specifically targeting a group will rise. If an email list from a bank leaks onto the internet, we can expect wave after wave of malicious email targeting those users and those attacks will be very successful. † These emails and the websites they link to do not generally contain any harmful content; the harm derives from convincing you to provide personal details. A phish attack is more likely to be delivered to the user if it does not carry a suspicious payload. However, some traditional email-borne viruses (such as W32/Mimail.j@MM) will also prompt you for information when they have infected your system. Therefore phish attacks may arrive in a benign form or may arrive in a malicious form. Both types may use vulnerabilities in email clients, web browsers and/or operating systems to make their attacks harder to detect. All antivirus products will detect traditional viruses and there is an increase in detections for benign, but obviously malicious, fakery (such as those that use particular operating system faults: http://vil.nai.com/vil/content/v_100927.htm). How To Protect Yourself- Do not click links in emails.
- If you feel you must click a link in an email, wait 24 hours after receiving the message. Phishing scams that rely on websites do not last long as they are discovered and shut down.
- When visiting your bank or online stores etc, open your web browser and enter the main address manually, eg. www.anz.com.au.
- Remember that banks and online stores should never ask you for your details over the phone or via email. Be vigilant against suspicious requests in emails, websites or by telephone.
- Check for a secure session before entering any private information. The address of the website should start with https:// and there should be a padlock icon in the bottom right-hand corner of the browser window or in the address bar:
 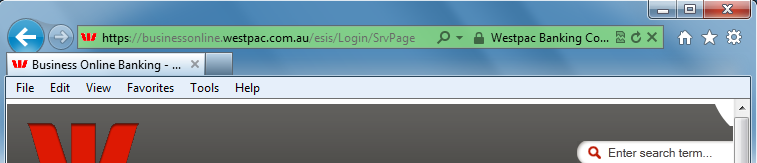
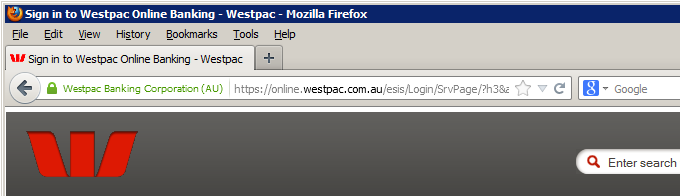
If you double-click the padlock icon the browser will show you the details of the certificate used to secure the site. - Be vigilant for certificate warnings. The presence of a certificate is not a guarentee. If you receive a warning such as this:
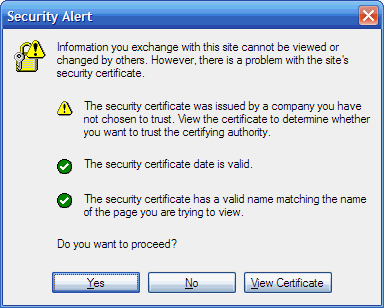 It means the certificate used is invalid in some way and you must make a judgement about whether to continue with whatever you are doing. If in doubt, choose No and exit the web browser. - Check for bad logins. If you log in to your bank's website, and the login fails and you are taken back to the bank's login page, you may have just given your details to a hacker and they have then sent you to the legitimate website. If you log in to the legitimate website, and you receive a warning that a previous login attempt failed, then you simply logged in incorrectly. If you do not receive a failed login warning, you may have been compromised. Change your online passwords immediately if this occurs.
- Change your online banking, shopping passwords regularly.
- Use different passwords for different services.
- Keep your web browser and operating system up to date with security patches by visiting http://windowsupdate.microsoft.com regularly or the appropriate vendor for your product. Spammers/hackers/phishers exploit faults in applications and operating systems which makes it easier for them to trick you. (However they can still trick you even if your system is perfectly secured.)
- Keep your anti-virus system up to date; some anti-virus products can detect certain fake emails and exploits used within emails.
- Review Cadzow Knowledge Base Article 1131 for a variety of security and antivirus resources.
Further Reading- CISA: https://www.cisa.gov/phishing-infographic
Footnotes† 25/01/2005 — This has now happened! A badly written web-based “opt-out” function provided by a popular e-commerce site has exposed a large number of email addresses. Since these addresses are all known to be users of that specific service, any phish attacks with this list will be very accurately targeted.
Copyright © 1996-2023 Cadzow TECH Pty. Ltd. All rights reserved.
Information and prices contained in this website may change without notice. Terms of use.
Question/comment about this page? Please email webguru@cadzow.com.au
|
